Trends in cyber risk
Criminals have turned hacking into a lucrative business
The business model of cybercrime has shifted significantly. Hackers have transitioned from selling stolen data and credit card information online to a much more effective and lucrative — stealing funds directly through funds transfer fraud and ransomware.
Data theft remains a critical risk that can result in all kinds of headaches and expenses, including regulatory fines, penalties, reputational harm, and client notifications and monitoring. Unfortunately, ransom payments and funds transfer fraud have quickly become the preferred tactics for criminals. Not only are they easier and faster to use, they result in much larger payouts.
Claims frequency increased 53% for professional services, including law firms. And law firms continue to fall victim to highly sophisticated attacks. Coalition predicts that phishing, exploitation of remote network access points, exploitation of unpatched software with known vulnerabilities, and weak credentials will continue to be the main causes of cyber incidents.
Most cyber-attacks will continue to be avoidable
Most cyber incidents and security failures (particularly the ones targeting small firms) are preventable. The most effective methods to mitigate cyber risk now and for the foreseeable future are all no-cost or extremely low-cost to implement.
- Enable these basic controls to secure email:
Sender Policy Framework (SPF) can prevent domain spoofing. It enables your mail server to determine when a message came from the domain that it uses.
Domain Keys Identified Mail (DKIM) ensures that the content of your emails remains trusted and hasn’t been tampered with or compromised.
Domain-based Message Authentication, Reporting and Conformance (DMARC) ties the first two protocols together with a consistent set of policies.
- Enable multi-factor authentication. This means, in addition to the use of a user ID and password to validate access to your email system, the use of at least one of the following methods of authentication:
- a hardware or software token or access card;
- third party authentication applications providing time-bound, one-time codes, by a method other than text messaging; or
- text messaging authentication.
In the event of a claim on the Coalition policy, the largest applicable Retention amount may be reduced by 50% subject to a maximum reduction of $10,000, provided that multi-factor authentication was enabled and required at the time of the applicable event.
- Frequently patch software.
Looking ahead
- Ransomware will remain the single biggest threat for all organizations;
- The cyber insurance market will continue to harden throughout the year;
- Supply chain attacks will be more common;
- Government regulation and scrutiny is expected to increase; and
- Most cyber attacks will continue to be easily avoidable.
|
Law firms’ most common cyber risks
According to the Global Cyber Alliance, 43% of cyber-attacks target small businesses, who often don’t have the security and technical expertise of larger organizations. Coalition’s cybersecurity guide will be particularly useful for small to medium law firms that want specific and actionable recommendations to protect their firm: 2022 Coalition General Security Recommendations. We strongly recommend that you review the guide to ensure that your firm is using standard cybersecurity practices and procedures. The guide will also be helpful when you review your firm’s dashboard information from Coalition: Your dashboard.
The most common cyber risks that law firms face are business email compromise, funds transfer fraud, and ransomware – they can result in serious consequences to firms and their clients.
1. Business email compromise
Any law firm that uses email (i.e., all of them) is susceptible to business email compromise (BEC). Once an attacker gets access to your email it’s game over. Business email is a treasure trove of sensitive information that criminals use to: pretend to be a client or people in your firm or bank, redirect money, and deploy ransomware.
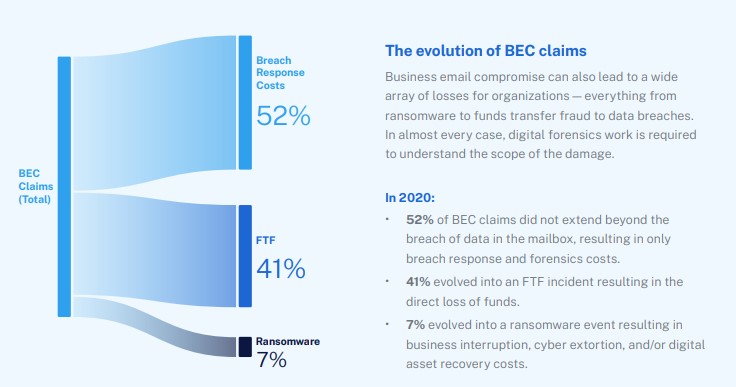
How to combat business email compromise
- Multi-factor authentication (MFA). MFA is common across technology platforms these days and should be turned on across all business email accounts and other key business software such as VPNs, financial accounts, and any other application where sensitive information is stored. While it is nearly impossible to prevent phishing entirely, using MFA can stop criminals in their tracks. Usually through brute-force attacks (criminals trying multiple username and password combinations in quick succession) or through stolen credentials from the dark web (people reusing username and password combinations), criminals can quickly gain access to business email accounts without this extra piece of security. Once in, the criminal can reroute money to fraudulent bank accounts, or create a ransomware event or major privacy breach.
- Password management. Encourage employees to use a password manager (e.g., Lastpass, 1Password, or the password managers built into web browsers like Chrome or Safari). Using strong, unique passwords for each of the services you use can help prevent common criminal techniques such as “brute forcing” or “credential stuffing.”
- Email security. Email is the single most targeted point of entry into an organization for a criminal hacker, and the implementation of these email security measures can be done quickly, and for free. Implement basic email security measures including SPF, DKIM, DMARC, and an anti-phishing solution.
- Other tips.
- If you sense anything unusual in an email, hover over the name of the person sending you the email to ensure that the email address is correct. For example, an email from someone within your firm should have the same domain you use.
- If you unexpectedly receive a link or attachment – even if it is from someone you know – or sense anything unusual, call the sender using the telephone number you have on file (not the number listed in the message) to confirm the message is legitimate. Do not verify an email with an email.
- If you open a link or attachment that you should have avoided, or a box opens that asks for your password or other information, stop. Close out. Immediately call your IT professional, inform your law firm staff, and report the incident to Coalition.
- Avoid using public, unsecured Wi-Fi and do not access private or confidential information in public spaces. The person sipping a latte to your left may be stealing your passwords.
2. Funds transfer fraud
Funds transfer fraud (FTF) is among the easiest ways to monetize cyber crime. Unlike ransomware, which requires more sophisticated attack techniques and specialized malware, FTF is most often perpetrated through phishing and email compromise followed by social engineering. Social engineering fraud occurs when a fraudster succeeds in having a lawyer, for example, transfer client funds to the fraudster based on an intentionally misleading representation of facts.
Common funds transfer fraud techniques are:
- Invoice manipulation occurs when a client the firm may be dealing with is tricked into paying an invoice from the firm that they believe is legitimate but has actually been manipulated to appear real. The client then refuses to pay the firm’s legitimate account when it comes. It can also occur in reverse – when a firm employee pays an invoice from a vendor that has been manipulated and sent to the firm by a cyber-criminal. Invoice manipulation is devious. Unlike run-of-the-mill phishing attacks, invoice manipulation takes time observing an organization’s billing and payment processes and habits with third parties.
- Look-alike domains are domain names that closely resemble the domain name of a trusted website, for example by swapping letters around or substituting common characters. In this day and age, most of us are wary about clicking links that we don’t trust, and so look-alike domain names are designed to make it non-obvious that a link or message is coming from a malicious domain or sender. In advance of a social engineering attack, it is common to see criminal actors registering domains similar to the victim’s to ultimately phish the victim, or to perpetuate funds transfer fraud or business email compromise. Monitor look-alike domains on your firm’s dashboard provided to you by Coalition: Your dashboard.
- Email spoofing is the creation of an email with a forged sender address. Criminals spoof emails in the hopes of duping the recipient (i.e., the victim) into thinking the email originated from a trusted source. In the context of FTF, it is a technique that is used to spear phish, impersonating the email of a CEO/executive, vendor, or customer in an effort to trick the victim into wiring funds.
How to combat funds transfer fraud
Today, it is no longer safe to assume that email is a secure means of communication. Defined procedures for handling new payment instructions and change in payment requests are the primary defense. These procedures should include:
- Confirm instructions. Call the requesting party on a known good number to confirm the request. Never use the contact information provided in an email requesting a change. Even if the request is from another law firm, you should call to confirm that the instructions to transfer funds are legitimate.
- Double check. Use verification procedures like defined two-party approval for transfers, and have a second person review any payment detail changes.
If an FTF does occur, quick action is essential — the sooner an incident is reported to Coalition,the more likely they can cancel the transaction or claw back funds before the attackers withdraw them.
3. Ransomware
Ransomware attacks often result in significant interruptions to ongoing business activities. The process to recover and restore business operations, even when system backups are readily available, can be complex and time-intensive. What’s unfortunate is that small and mid-size law firms are impacted more often than larger ones — and they may be less able to defend themselves and bounce back quickly.
How to combat ransomware
- Email security like spam filtering and user training is critically important, as ransomware can be installed when users open a suspicious attachment or visit a malicious website. A robust cybersecurity program is also crucial to ensure technical vulnerabilities like old, unpatched software or insecure remote access tools are unavailable for attackers to exploit.
- Ensure RDP ports are protected and unused ones are closed. Remote Desktop Protocol (RDP) allows users to access their office desktop and computing resources remotely. While convenient, especially in the age of working from home, it can also make businesses extremely vulnerable to ransomware attacks if not configured properly. An open RDP ports is the most common cause of ransomware attacks. If you must use RDP access, secure it behind a virtual private network and multi-factor authentication.
- Routine backups. Regularly back up your systems and information, and store backups in an “off-site” location. Off-site doesn’t have to mean physically off-site, but in a location that is not connected to your main business network. This will make it far more difficult for a criminal hacker to delete or encrypt your backups.
|